This TN explains in detailed steps how to connect to a Secured Cloudera CDH cluster using Kerberos authentication. This TN applies to Strategy 10.3 and later versions only. Due to known issues Strategy Secure Enterprise 10.3 relies on the Cloudera ODBC driver when connecting to Hive on Cloudera CDH from a Linux/UNIX Intelligence Server. The Strategy ODBC Driver for Hive should not be used to connect to Hive on Cloudera CDH from a Linux/UNIX Intelligence Server.
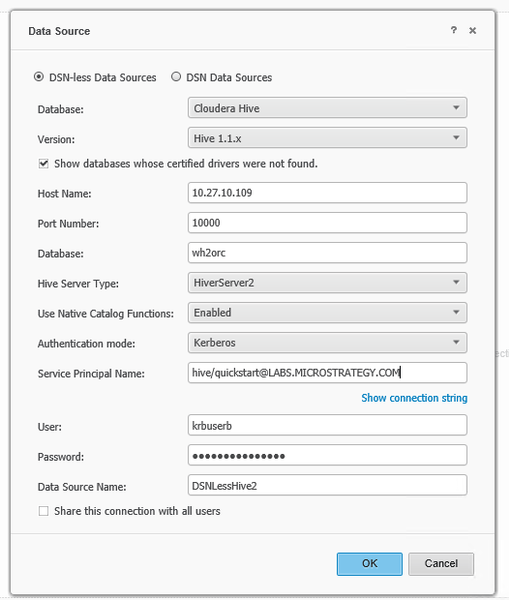
Install the Cloudera Hive ODBC Driver and configure Strategy connectivity settings
yum --nogpgcheck localinstall ClouderaHiveODBC-2.5.16.1005-1.el6.x86_64.rpm
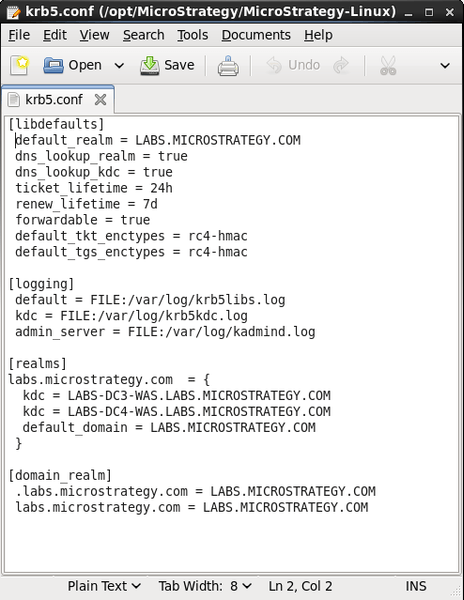
export KRB5_CONFIG=/etc/krb5.conf
export KRB5_CONFIG=/opt/Strategy/Strategy-Linux/krb5.conf
-sh-4.1$ kinit krbuserb@LABS.Strategy.COM Password for krbuserb@LABS.Strategy.COM: -sh-4.1$ klist Ticket cache: FILE:/tmp/krb5cc_126431806 Default principal: krbuserb@LABS.Strategy.COM Valid starting Expires Service principal 03/07/16 07:57:37 03/07/16 17:57:47 krbtgt/LABS.Strategy.COM@LABS.Strategy.COM renew until 03/14/16 08:57:37 -sh-4.1$
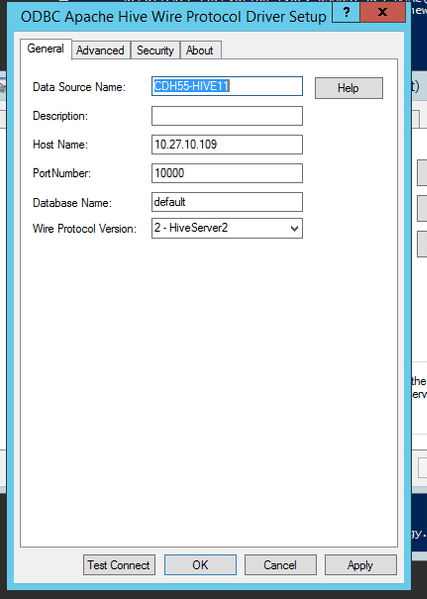
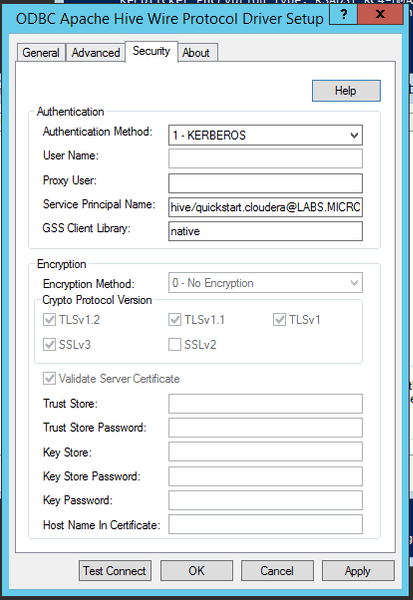
[ODBC Data Sources] Cloudera Hive=Cloudera ODBC Driver for Apache Hive 64-bit [Cloudera Hive] Driver=/opt/cloudera/hiveodbc/lib/64/libclouderahiveodbc64.so Description=Cloudera ODBC Driver for Apache Hive (64-bit) DSN DriverUnicodeEncoding=2 HOST=quickstart.cloudera PORT=10000 Schema=default FastSQLPrepare=0 UseNativeQuery=0 HiveServerType=2 AuthMech=1 KrbHostFQDN=quickstart.cloudera KrbServiceName=hive KrbRealm=LABS.Strategy.COM
[Cloudera ODBC Driver for Apache Hive] Driver=/opt/cloudera/hiveodbc/lib/64/libclouderahiveodbc64.so Description=Hive Driver Setup=/opt/cloudera/hiveodbc/lib/64/libclouderahiveodbc64.so APILevel=2 ConnectFunctions=YYY DriverODBCVer=1.0 FileUsage=0 SQLLevel=1
... DriverManagerEncoding=UTF-8 ErrorMessagesPath=/opt/cloudera/hiveodbc/ErrorMessages/ LogLevel=0 LogPath= SwapFilePath=/tmp ... # SimbaDM / unixODBC ODBCInstLib=libodbcinst.so
# Environment variable for Kerberos V5 configuration file
KRB5_HOME=/opt/Strategy/Strategy-Linux
export KRB5_HOME
KRB5_CONFIG=${KRB5_HOME:?}/krb5.conf
export KRB5_CONFIG
-sh-4.1$ whoami TECH_SERVICES\krbuserb -sh-4.1$ cd /opt/Strategy/Strategy-Linux/bin -sh-4.1$ ./mstrdbquerytool
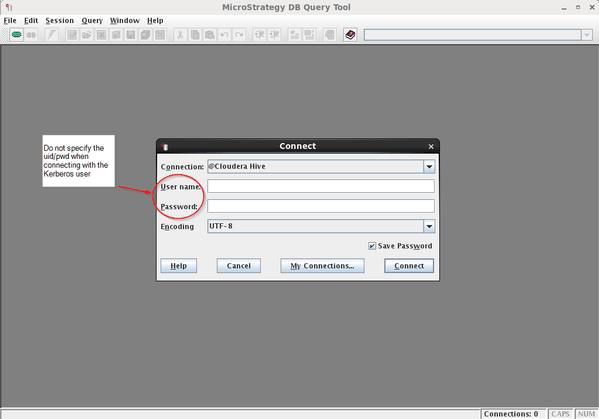
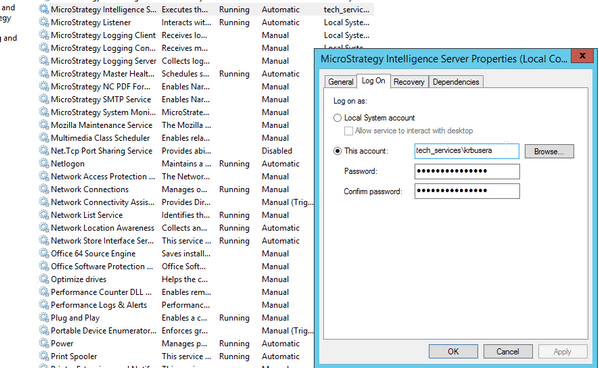
To make Kerberos secured warehouse connections to CDH/Hive the Strategy Intelligence Server process must run under the Kerberos user's account
-sh-4.1$ whoami TECH_SERVICES\krbuserb -sh-4.1$ cd /opt/Strategy/Strategy-Linux/bin -sh-4.1$ ./mstrcfgwiz
# ps -ef | grep MSTRSvr root 6890 6873 0 08:47 pts/4 00:00:00 grep MSTRSvr krbuserb 21173 19473 0 Mar04 ? 00:02:42 /opt/Strategy/Strategy-Linux/install/IntelligenceServer/bin/MSTRSvr -w /opt/Strategy/Strategy-Linux//IntelligenceServer -t status-iserver.xml /opt/Strategy/Strategy-Linux/install/lib/libMSTRSvr2.so -n CastorServer
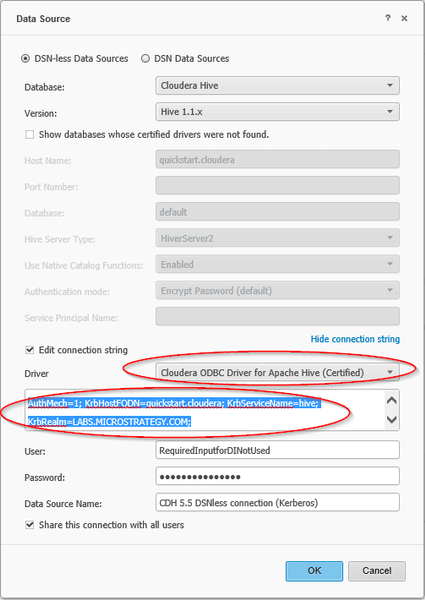
Sample DSN-less connection string:
DRIVER={Cloudera ODBC Driver for Apache Hive}; Host=quickstart.cloudera; Port=10000; Schema=default; HiveServerType=2;UseNativeCatalogFunctions=1; AuthMech=1; KrbHostFQDN=quickstart.cloudera; KrbServiceName=hive; KrbRealm=LABS.Strategy.COM;