In Strategy Web ASP, it is observed that the application accepts a pre-defined "ASP.NET_SessionId" and does not issue a new one upon a new user session login.
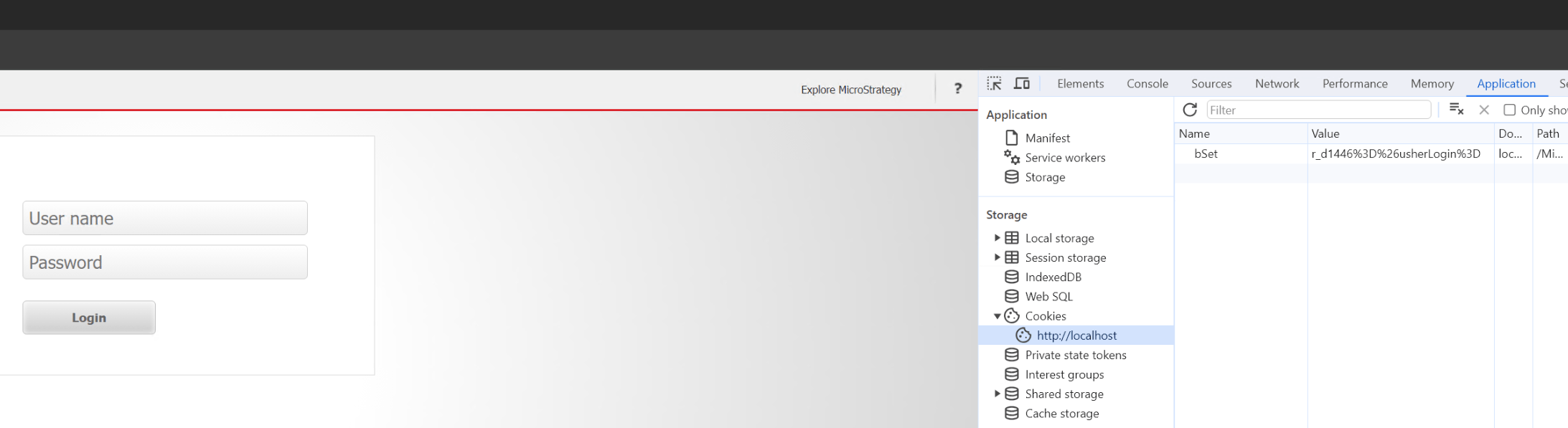
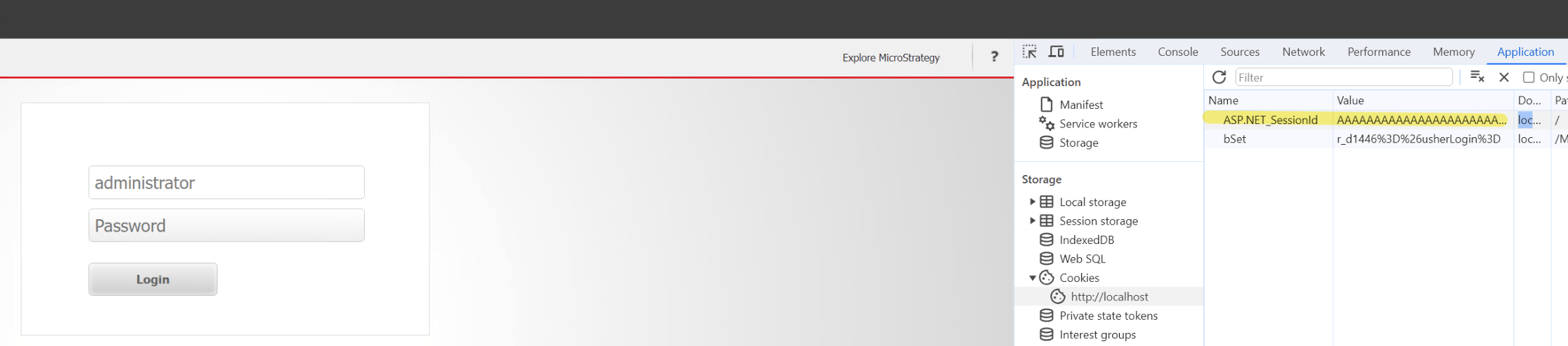
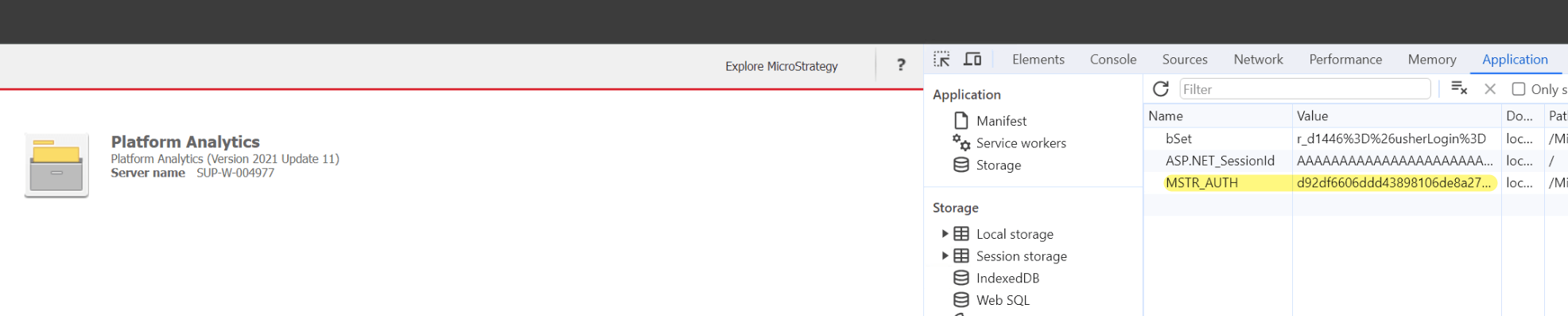
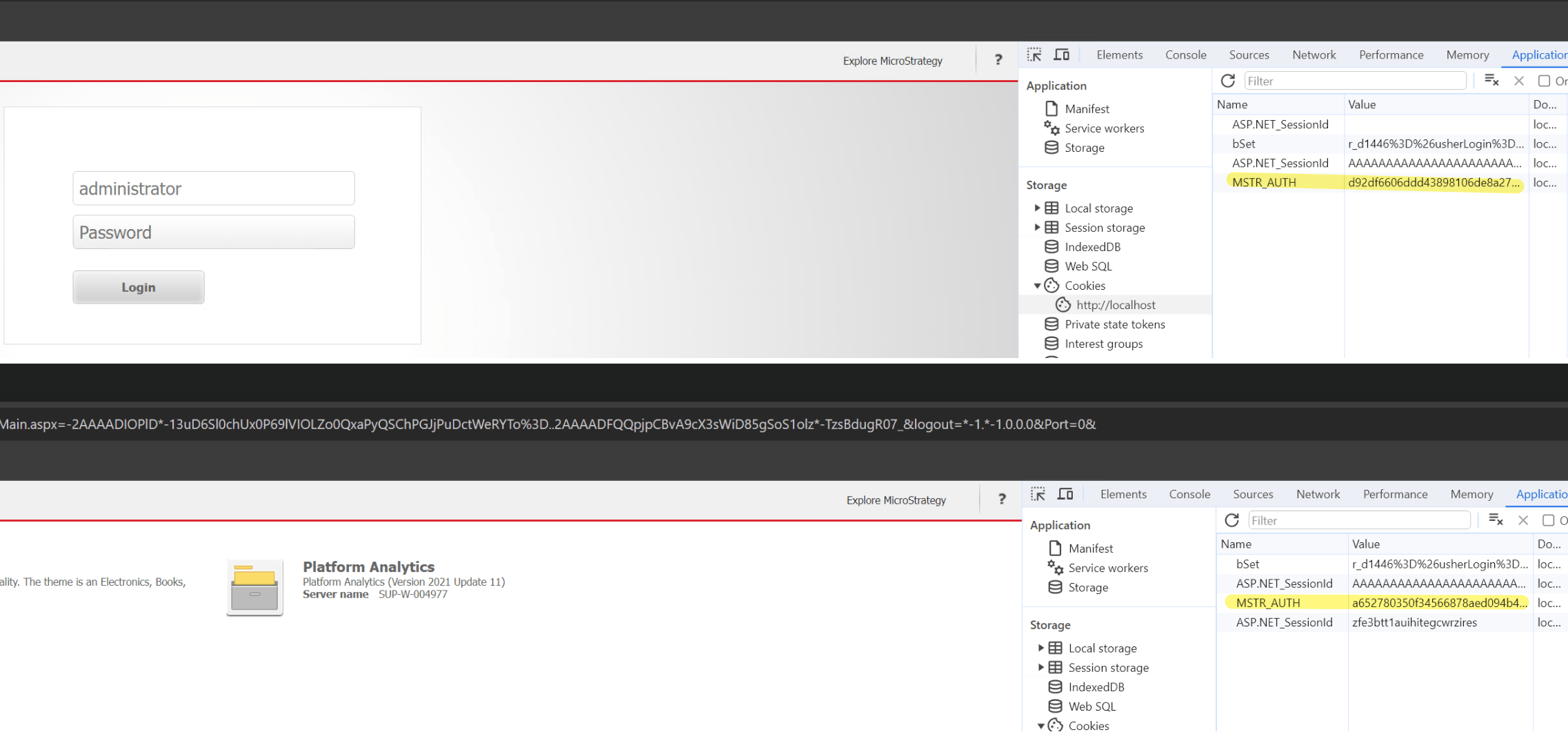
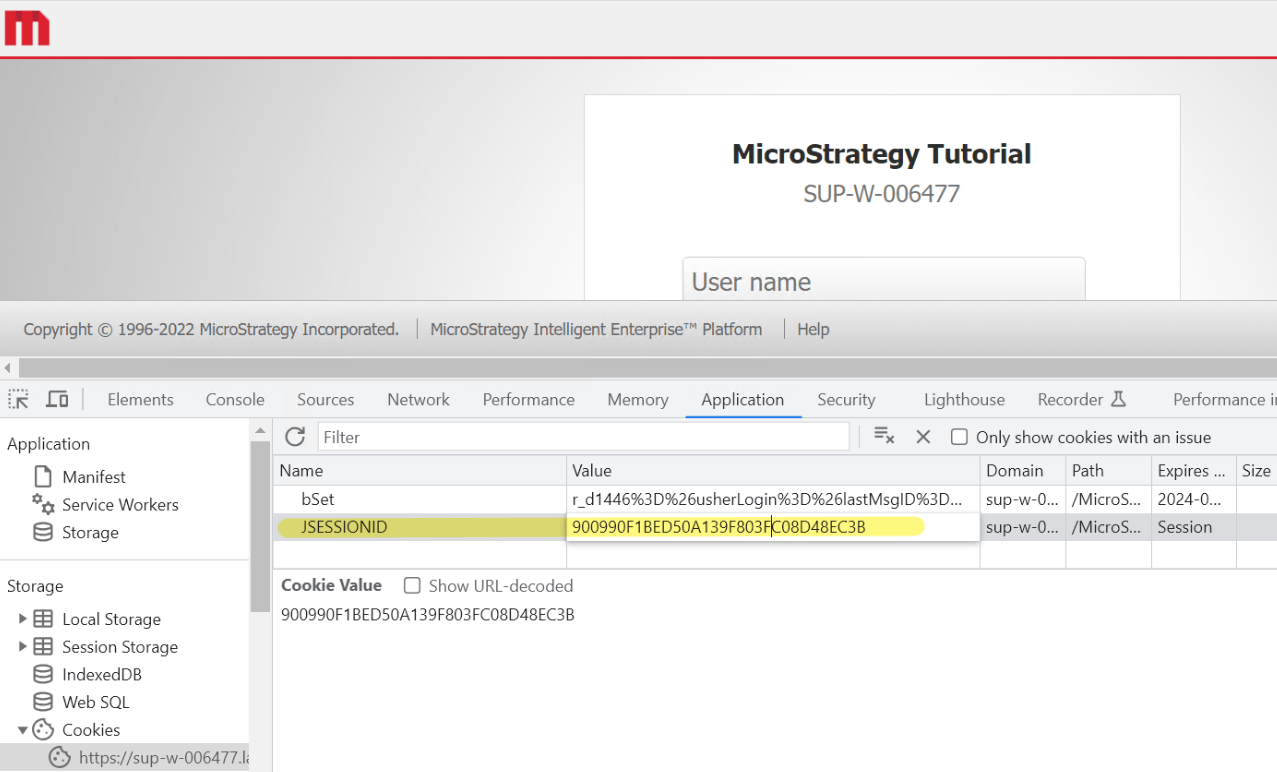
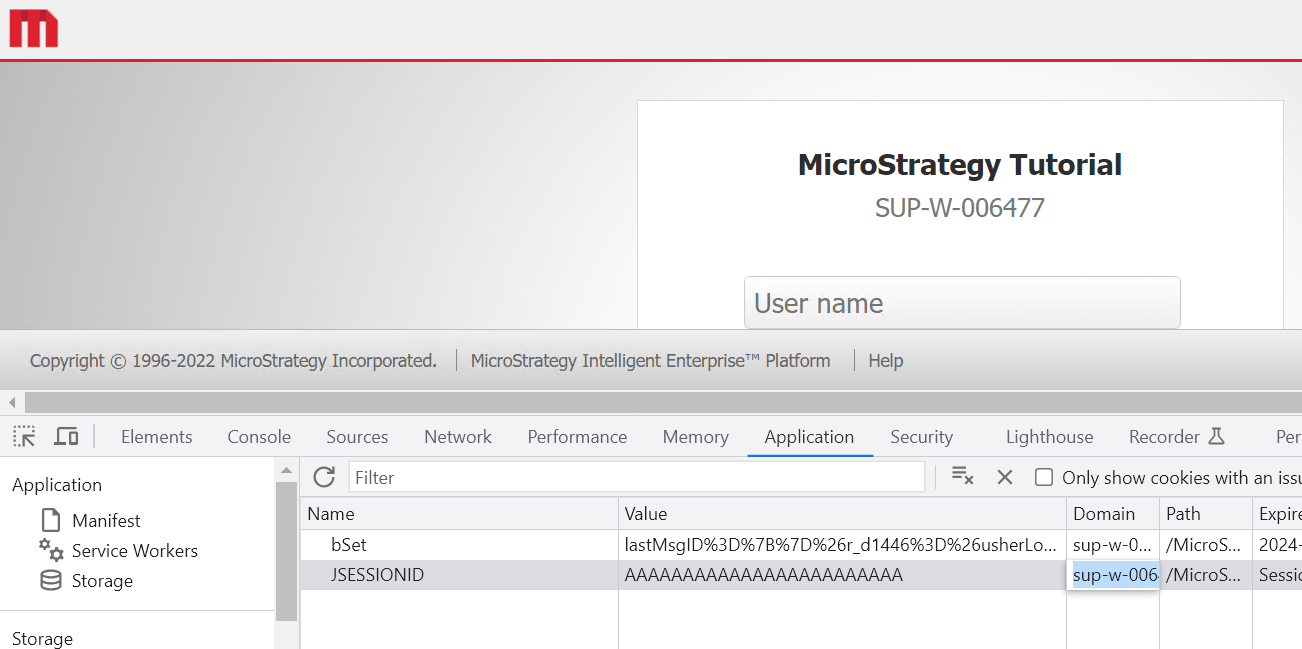
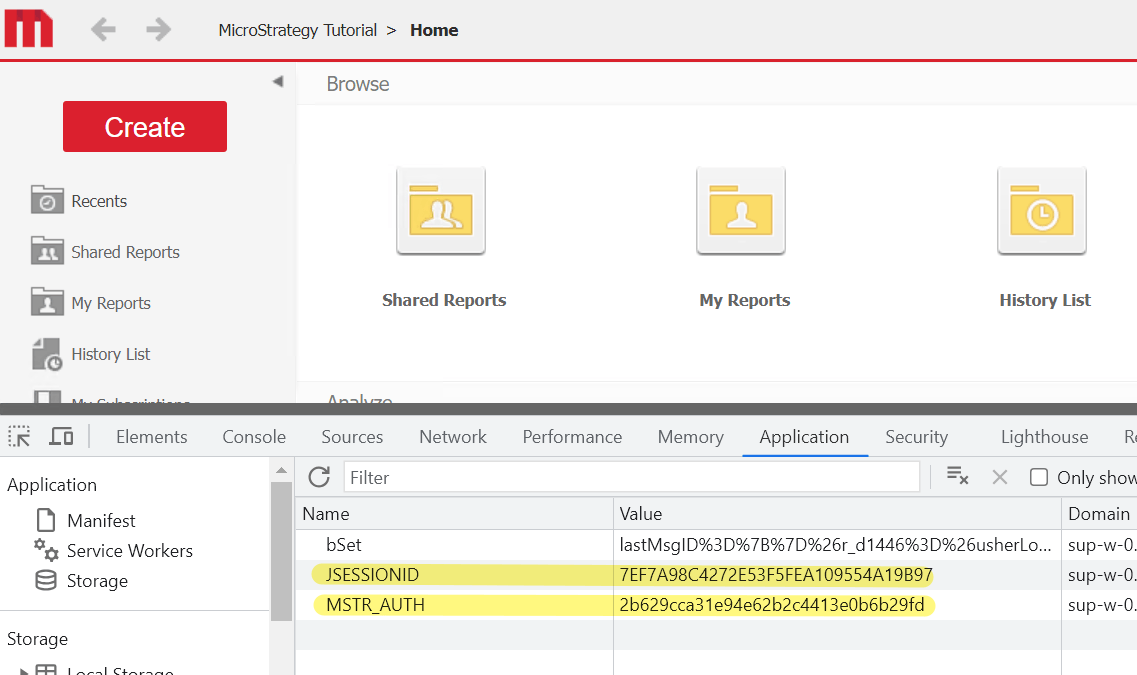
The MSTR_AUTH cookie is a secondary token which mitigates session fixation and hijacking.
Users should have both valid JSESSIONID/ASP.Net_SessionId and MSTR_AUTH in order to access Strategy Web successfully.